
Is Your Dallas IT Services Company On The Ball?
Discover why Aspire Tech is a top choice for Dallas IT services. Learn 5 reasons businesses trust Aspire Tech for proactive, reliable IT support and tailored solutions.
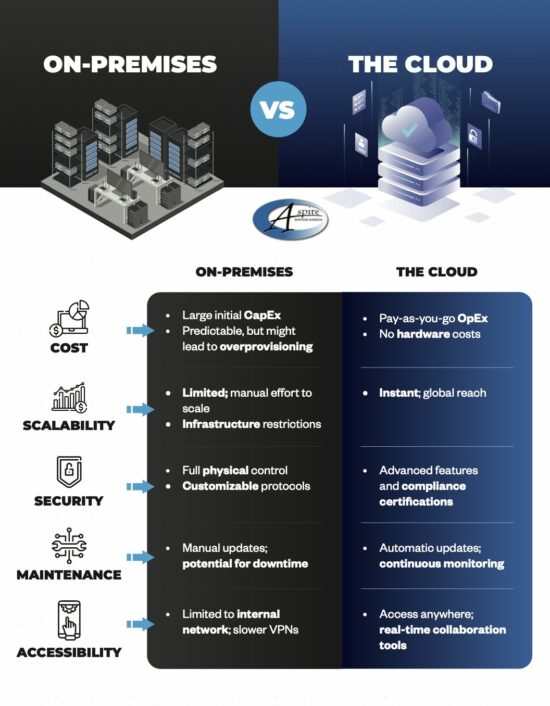
Why Dental Offices Throughout Dallas Must Consider Cloud Servers
Discover why dental offices in Dallas are turning to cloud servers for enhanced data security, cost efficiency, and streamlined operations. Learn how cloud technology can transform your practice.

Aspire Tech Releases 2024 Cloud Services Guide for Dallas & Fort Worth Dental Practices
Discover Aspire Tech’s 2024 Cloud Services Guide tailored for dental practices in Dallas & Fort Worth. Enhance your clinic’s efficiency and security with cutting-edge cloud solutions.

Dallas Dental Clinics Must Comply With Texas Data Privacy and Security Act (TDPSA) Starting July 1, 2024
Learn how the Texas Data Privacy and Security Act (TDPSA) impacts dental clinics, ensuring compliance with stringent data protection and privacy regulations. Discover best practices for safeguarding patient information and maintaining robust security standards in your dental practice.

Dallas Dental Practices And The AI Revolution
Discover how Dallas dental practices are embracing the AI revolution with Aspire Tech. Learn how cutting-edge technology is transforming patient care and streamlining operations for a brighter, healthier future.

Do You Love Your Dental IT Support Company?
Discover the ultimate IT partner for your Texas dental practice! Explore expert services tailored to streamline your operations, enhance security, and elevate patient care. Trust in reliable tech solutions designed specifically for your practice’s success.

How Ransomware Threatens Dental Clinics
Discover the alarming rise of ransomware threats targeting dental clinics in Dallas. Uncover the vulnerabilities that make these healthcare practices susceptible and learn essential cybersecurity measures to safeguard patient data and preserve the integrity of dental services.

Dallas Dental Offices
Be Careful Of The Cyber Grinch
Guard your Dallas dental office against the looming cyber threat! Aspire Technical Solutions offers cutting-edge cybersecurity solutions to keep your practice safe from the digital Grinch. Don’t let cyber vulnerabilities steal your peace of mind – trust Aspire for robust protection and seamless defense. Secure your dental practice with our expertise today!

Your Trusted Dallas IT Services Partner
Aspire Technical Solutions: Your trusted Dallas IT partner. From help desk to digital transformation, we provide scalable solutions for seamless operations. Anticipate and overcome challenges while we manage your IT infrastructure. Focus on your business; let Aspire drive your success with tailored, evolving IT services.
